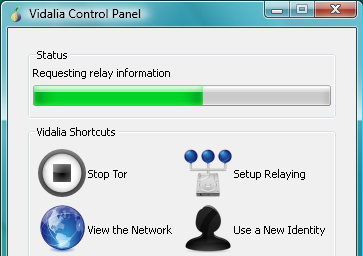
- Both the Tor Browser and access to the Tor network are free. Tor Download Mac We extracted and opened the Tor Browser, which includes the Vidalia Control Panel, a small dialog box for configuring and managing your connection to the Tor network.
- Free tor browser for mac 10.5.8 download software at UpdateStar - The Tor software protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world: it prevents somebody watching your Internet connection from learning what sites you visit, it.
5 free downloads to keep your PC or Mac secure. One of the most popular inconspicuous tools available is The Onion Router or Tor, for short. The free Ghostpress download scans for.

Try these downloads recommended by Kim Komando to keep your PC or Mac safe. (iStock)
The FBI has seen a significant spike in cybercrime reports since the onset of the COVID-19 pandemic. Hackers, scammers, and snoops are having a field day. Be sure to check for any updates to your gear.
A bug has been found in 79 different popular router models that lets hackers remotely take over your devices. Tap or click here for the complete list of affected routers and how to protect your network.
Tor Browser Download For Apple
Phones are targets, too. Tap or click here for a specialized app that will tell you if your iPhone has been hacked.
Although you're frustrated over recent national events, it's no time to let your guard down. Here a few ways to safeguard your digital life.
1. Use the internet anonymously
Are you tired of advertisers, snoops, and Big Tech tracking your every move online? One of the most popular inconspicuous tools available is The Onion Router or Tor, for short. Initially developed in the mid-1990s by the U.S. Navy to protect U.S. online communications, it is now a free global network for public use.
By rerouting your internet traffic through Tor, you can make it difficult for would-be snoops to trace your location and online activity back to you. From privacy advocates to journalists to internet denizens who are concerned about surveillance and monitoring, Tor is the go-to tool for web anonymity.
However, setting up your computer to exclusively route its traffic through Tor can be a challenge. Thankfully, there's an easy-to-use web browser that will automatically route all its traffic through Tor even without advanced computer and networking knowledge.
2. Don't let malware take over your system

Antimalware programs are essential for scanning and removing harmful files from your computer. Microsoft's Windows Defender comes with your PC. It scans your computer for malware, quarantines malicious files and removes them with just a few clicks.
Make sure you're using the latest version. Tap or click here to get the latest Windows Defender updates.
Although Apple does not offer built-in malware protection for Macs, you still need it. In about 30 seconds, Malwarebytes for Mac identifies and removes malicious files. There is a pay version, but the free option is sufficient for most people.
3. Let IBM control your DNS
The internet's Domain Name System (DNS) directs you to specific websites when you enter a domain name in your browser. It's why you can type a site's name (for example, Archive.org) rather than the site's cumbersome IP address (207.241.224.2). Your internet service provider automatically assigns your DNS settings, but hackers can hijack them to redirect traffic to malicious websites.
Instead, use Quad9 maintained by IBM and The Global Cyber Alliance. Once set up, the free and fast DNS Quad9 service instantly checks any site you wish to visit against IBM X-Force's threat intelligence database of over 40 billion analyzed webpages and images.
Mac Tor Browser

Quad9 blocks unauthorized DNS redirects and remote hosts, too. It's simple to set up, and there is no program to download.
4. Make sure no one is spying on you
Keyloggers collect everything that you do on your computer and share it with hackers who control them. One mistake opening an attachment, visiting a rogue website, or hitting the wrong link and you're a victim. It's a simple way for hackers to steal your data and account credentials.
The free Ghostpress download scans for existing keyloggers on your computer and offers real-time protection. It runs in the background while you type and also blocks background attempts to record your activities.
Are you using a Mac? Tap or click here for tips on spotting and removing keyloggers.
5. Only use encrypted connections
When shopping online, you know to look for web addresses that start with 'https://'. This assures you that the website is transferring data over a secure encrypted connection. You'll also see a lock icon in your browser's address bar.
This encryption guards against hijacking and malicious hacking attempts, but not every site has made the switch. Take matters into your own hands. You can remember only to visit mainstream sites and look for the lock.
Alternatively, add the free HTTPS Everywhere browser extension to your security arsenal. It rewrites your web requests as secure, even if the website you visit isn't adequately encrypted.
And one more, don't forget your cameras.
We've all heard the horror stories of someone hacking into a security camera watching over a home or nursey. Take action now before you become a victim. Many security cameras offer increased security settings and two-factor authentication.
What digital lifestyle questions do you have? Call Kim's national radio show and tap or click here to find it on your local radio station. You can listen to or watch The Kim Komando Show on your phone, tablet, television or computer. Or tap or click here for Kim's free podcasts.
Free Tor Download For Mac
Copyright 2020, WestStar Multimedia Entertainment. All rights reserved.
Learn about the latest technology on the Kim Komando Show, the nation's largest weekend radio talk show. Kim takes calls and dispenses advice on today's digital lifestyle, from smartphones and tablets to online privacy and data hacks. For her daily tips, free newsletters and more, visit her website at Komando.com.
In case you weren't aware, your Internet Service Provider (as well as other less than reputable parties), can monitor your every move on the internet. This means every website you visit, every file you download, it knows what you're up to. Luckily, there is a tool available that can keep your online activities under wraps. It's called the Tor Browser.
What is Tor?
The Tor website explains it best:
The Tor network is a group of volunteer-operated servers that allows people to improve their privacy and security on the Internet. Tor's users employ this network by connecting through a series of virtual tunnels rather than making a direct connection, thus allowing both organizations and individuals to share information over public networks without compromising their privacy. Along the same line, Tor is an effective censorship circumvention tool, allowing its users to reach otherwise blocked destinations or content. Tor can also be used as a building block for software developers to create new communication tools with built-in privacy features.
By making use of the Tor network, users can safely and privately navigate the web. We'll warn you upfront that using Tor will slow your internet connection a bit, so using it for streaming and such probably won't be a satisfactory experience. But for connections where privacy is a must, Tor is a great option.
Installing Tor on Your Mac
The easiest way to install the Tor software on your Mac is to download the Tor Bundle form the Tor website. Visit the Tor Bundle Download Page. The website should recognize that you are on a Mac, and offer up a link to click to begin the download. Just click that rather large purple button to begin the download.
After the download is complete, open the folder you downloaded the install app to, (likely your 'Downloads' directory), and double-click the file to begin the installation.
Drag the TorBrowser icon to your Applications folder to install it. To run Tor, simply open your Applications folder, find the icon, and double-click it to run the app. You'll likely be asked if you really want to open the app the first time you run it. Just click the 'Open' button and the Tor Browser will load.
- Both the Tor Browser and access to the Tor network are free. Tor Download Mac We extracted and opened the Tor Browser, which includes the Vidalia Control Panel, a small dialog box for configuring and managing your connection to the Tor network.
- Free tor browser for mac 10.5.8 download software at UpdateStar - The Tor software protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world: it prevents somebody watching your Internet connection from learning what sites you visit, it.
5 free downloads to keep your PC or Mac secure. One of the most popular inconspicuous tools available is The Onion Router or Tor, for short. The free Ghostpress download scans for.
Try these downloads recommended by Kim Komando to keep your PC or Mac safe. (iStock)
The FBI has seen a significant spike in cybercrime reports since the onset of the COVID-19 pandemic. Hackers, scammers, and snoops are having a field day. Be sure to check for any updates to your gear.
A bug has been found in 79 different popular router models that lets hackers remotely take over your devices. Tap or click here for the complete list of affected routers and how to protect your network.
Tor Browser Download For Apple
Phones are targets, too. Tap or click here for a specialized app that will tell you if your iPhone has been hacked.
Although you're frustrated over recent national events, it's no time to let your guard down. Here a few ways to safeguard your digital life.
1. Use the internet anonymously
Are you tired of advertisers, snoops, and Big Tech tracking your every move online? One of the most popular inconspicuous tools available is The Onion Router or Tor, for short. Initially developed in the mid-1990s by the U.S. Navy to protect U.S. online communications, it is now a free global network for public use.
By rerouting your internet traffic through Tor, you can make it difficult for would-be snoops to trace your location and online activity back to you. From privacy advocates to journalists to internet denizens who are concerned about surveillance and monitoring, Tor is the go-to tool for web anonymity.
However, setting up your computer to exclusively route its traffic through Tor can be a challenge. Thankfully, there's an easy-to-use web browser that will automatically route all its traffic through Tor even without advanced computer and networking knowledge.
2. Don't let malware take over your system
Antimalware programs are essential for scanning and removing harmful files from your computer. Microsoft's Windows Defender comes with your PC. It scans your computer for malware, quarantines malicious files and removes them with just a few clicks.
Make sure you're using the latest version. Tap or click here to get the latest Windows Defender updates.
Although Apple does not offer built-in malware protection for Macs, you still need it. In about 30 seconds, Malwarebytes for Mac identifies and removes malicious files. There is a pay version, but the free option is sufficient for most people.
3. Let IBM control your DNS
The internet's Domain Name System (DNS) directs you to specific websites when you enter a domain name in your browser. It's why you can type a site's name (for example, Archive.org) rather than the site's cumbersome IP address (207.241.224.2). Your internet service provider automatically assigns your DNS settings, but hackers can hijack them to redirect traffic to malicious websites.
Instead, use Quad9 maintained by IBM and The Global Cyber Alliance. Once set up, the free and fast DNS Quad9 service instantly checks any site you wish to visit against IBM X-Force's threat intelligence database of over 40 billion analyzed webpages and images.
Mac Tor Browser
Quad9 blocks unauthorized DNS redirects and remote hosts, too. It's simple to set up, and there is no program to download.
4. Make sure no one is spying on you
Keyloggers collect everything that you do on your computer and share it with hackers who control them. One mistake opening an attachment, visiting a rogue website, or hitting the wrong link and you're a victim. It's a simple way for hackers to steal your data and account credentials.
The free Ghostpress download scans for existing keyloggers on your computer and offers real-time protection. It runs in the background while you type and also blocks background attempts to record your activities.
Are you using a Mac? Tap or click here for tips on spotting and removing keyloggers.
5. Only use encrypted connections
When shopping online, you know to look for web addresses that start with 'https://'. This assures you that the website is transferring data over a secure encrypted connection. You'll also see a lock icon in your browser's address bar.
This encryption guards against hijacking and malicious hacking attempts, but not every site has made the switch. Take matters into your own hands. You can remember only to visit mainstream sites and look for the lock.
Alternatively, add the free HTTPS Everywhere browser extension to your security arsenal. It rewrites your web requests as secure, even if the website you visit isn't adequately encrypted.
And one more, don't forget your cameras.
We've all heard the horror stories of someone hacking into a security camera watching over a home or nursey. Take action now before you become a victim. Many security cameras offer increased security settings and two-factor authentication.
What digital lifestyle questions do you have? Call Kim's national radio show and tap or click here to find it on your local radio station. You can listen to or watch The Kim Komando Show on your phone, tablet, television or computer. Or tap or click here for Kim's free podcasts.
Free Tor Download For Mac
Copyright 2020, WestStar Multimedia Entertainment. All rights reserved.
Learn about the latest technology on the Kim Komando Show, the nation's largest weekend radio talk show. Kim takes calls and dispenses advice on today's digital lifestyle, from smartphones and tablets to online privacy and data hacks. For her daily tips, free newsletters and more, visit her website at Komando.com.
In case you weren't aware, your Internet Service Provider (as well as other less than reputable parties), can monitor your every move on the internet. This means every website you visit, every file you download, it knows what you're up to. Luckily, there is a tool available that can keep your online activities under wraps. It's called the Tor Browser.
What is Tor?
The Tor website explains it best:
The Tor network is a group of volunteer-operated servers that allows people to improve their privacy and security on the Internet. Tor's users employ this network by connecting through a series of virtual tunnels rather than making a direct connection, thus allowing both organizations and individuals to share information over public networks without compromising their privacy. Along the same line, Tor is an effective censorship circumvention tool, allowing its users to reach otherwise blocked destinations or content. Tor can also be used as a building block for software developers to create new communication tools with built-in privacy features.
By making use of the Tor network, users can safely and privately navigate the web. We'll warn you upfront that using Tor will slow your internet connection a bit, so using it for streaming and such probably won't be a satisfactory experience. But for connections where privacy is a must, Tor is a great option.
Installing Tor on Your Mac
The easiest way to install the Tor software on your Mac is to download the Tor Bundle form the Tor website. Visit the Tor Bundle Download Page. The website should recognize that you are on a Mac, and offer up a link to click to begin the download. Just click that rather large purple button to begin the download.
After the download is complete, open the folder you downloaded the install app to, (likely your 'Downloads' directory), and double-click the file to begin the installation.
Drag the TorBrowser icon to your Applications folder to install it. To run Tor, simply open your Applications folder, find the icon, and double-click it to run the app. You'll likely be asked if you really want to open the app the first time you run it. Just click the 'Open' button and the Tor Browser will load.
You'll also be asked to modify some settings for the Tor setup the first time the app is run, but in most cases, no changes are needed, and you can just click the 'Connect' button to connect to the Tor network. There will be a short wait as the app configures itself and connects to the network.
When the Tor Browser opens, you'll see a message confirming you've correctly installed the Tor software. You can verify that everything is working correctly by clicking the 'Test Tor Network Settings' link on this webpage.
Downloads For Mac
A new page will display, congratulating you on having everything configured properly, and showing you what you IP address will appear to be to other parties. (It'll be different from your real one. That's part of the anonymity of Tor.)
Download Free Programs For Mac
You are now ready to browse the internet while enjoying the anonymity Tor provides. To get the most out of Tor, be sure to read the helpful tips the website offers for browsing with Tor. Quick tip, don't expect all of your internet traffic to by protected by Tor, only the traffic passing through the Tor browser is protected. Be sure to keep that in mind.
Download Tor Browser Free Mac
For more tips and tricks that can help you make better use of your Mac, iOS device, Apple Watch, or Apple TV, be sure to visit the 'How To' section of our website.
